Why Your Website Need SSL Encryption Security?
Nowadays everyone likes to purchase from the website, and online transaction is a big part of that. In a recent report, cybercrime found that more than 30,000 websites are infected every day with malware and their data stolen by unknown hackers. The primary reason for website hacking and malware attacks are using old version CMS (Content Management System) and plugin for long-time and sometimes not using SSL (Secure Sockets Layer) Certificate on the website.
Medium and Small scale business sites such as personal blogs, local stores, and local news sites are easy targets for online hackers because those website does not plan to spend on their website data security. Without encryption security, hackers can steal your private data such as email address, password, and credit card details and can easily misuse them. According to Wall Street Journal, the estimated loss from cybercrime is $100 billion every year. If you are running an online business or any online activity where customers need to share personal details, then your website needs SSL encryption protection.
SSL Certificate creates an encrypted connection between server and browser through a key pair (a public and a private key). These certificates also contain website owner information, which is known as "Subject.".
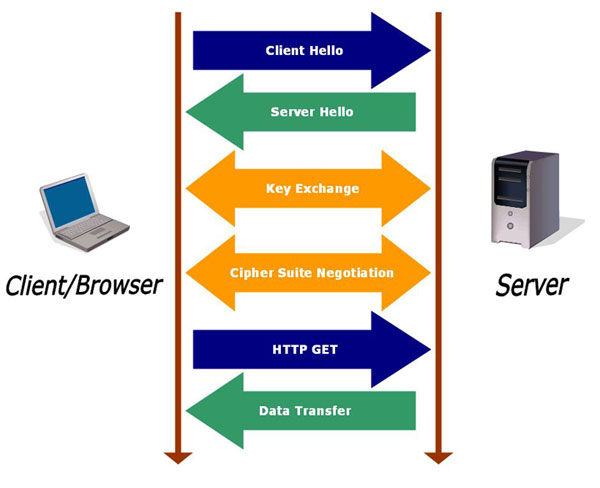 To get an SSL certificate, you need to first create a CSR (Code Signing Request) on your website hosting server. This process gives you two pair of keys (Public and Private Key) file.
Once you received the CSR data file, you need to send the public key file to SSL Certificate issuer also known as Certificate Authority or CA. When SSL Certificate issuer received the public key file, they create a structure to match your private key. The SSL Certificate issuer can never see your private key data.
After the completion of SSL certificate verification, when a browser tries to access your website protected by SSL certificate, the browser and server connect through SSL connection. Anything sends from the browser in encrypted form through public key can only decrypt from the private key install on the server.
To get an SSL certificate, you need to first create a CSR (Code Signing Request) on your website hosting server. This process gives you two pair of keys (Public and Private Key) file.
Once you received the CSR data file, you need to send the public key file to SSL Certificate issuer also known as Certificate Authority or CA. When SSL Certificate issuer received the public key file, they create a structure to match your private key. The SSL Certificate issuer can never see your private key data.
After the completion of SSL certificate verification, when a browser tries to access your website protected by SSL certificate, the browser and server connect through SSL connection. Anything sends from the browser in encrypted form through public key can only decrypt from the private key install on the server.
Any online business whether large, medium or small scale required SSL certificate to meet Card Payment Industry guidelines. PCI (Payment Card Industry) verify the SSL certificate is obtain from a trusted SSL authority and providing a secure private connection in the pages where customer needs to enter their personal details.

Replicate or fraud website do not get SSL certificate easily. If a visitor is completely aware of SSL protection, they will simply move from such untrusted website without any further action.

A Customer can easily check whether the website is secure from SSL certificate with the help of site seal and green bar. Website with SSL certificate will increase customer trust and confidence of online purchase.
What Happen When You Do Not Use Data Encryption

Medium and Small scale business sites such as personal blogs, local stores, and local news sites are easy targets for online hackers because those website does not plan to spend on their website data security. Without encryption security, hackers can steal your private data such as email address, password, and credit card details and can easily misuse them. According to Wall Street Journal, the estimated loss from cybercrime is $100 billion every year. If you are running an online business or any online activity where customers need to share personal details, then your website needs SSL encryption protection.
What is SSL Certificate
SSL Certificate creates an encrypted connection between server and browser through a key pair (a public and a private key). These certificates also contain website owner information, which is known as "Subject.".
How SSL Certificate Works

Benefits of SSL Certificate
Essential in Online Payment System:
Any online business whether large, medium or small scale required SSL certificate to meet Card Payment Industry guidelines. PCI (Payment Card Industry) verify the SSL certificate is obtain from a trusted SSL authority and providing a secure private connection in the pages where customer needs to enter their personal details.
Protection against Phishing:

Replicate or fraud website do not get SSL certificate easily. If a visitor is completely aware of SSL protection, they will simply move from such untrusted website without any further action.
Improve Customer Trust:

A Customer can easily check whether the website is secure from SSL certificate with the help of site seal and green bar. Website with SSL certificate will increase customer trust and confidence of online purchase.
Types of SSL Certificate
There are various types of SSL certificate products and brands are currently available in the market, based on your website type and requirement you can buy SSL certificate. For better understanding, you can also visit SSL Certificate Finder page.Some Popular SSL Certificate Products
- Single Domain SSL Certificate
- Multi Domain SSL Certificate
- Extended Validation (EV) Certificate
- Organization Validation SSL Certificate
- Wildcard SSL Certificate